Simplify ISPF login with
c3270andx3270if, and harness the power of ISPF as an API to z/OS UNIX withs3270.
z/OS, a robust mainframe operating system, not only provides a z/OS UNIX environment but also offers a wide range of MVS functions through various interfaces. Many of these MVS functions can only be accessed via ISPF, which is officially known as the z/OS TSO/ISPF interface, but also commonly referred to as the “green screen.” And despite z/OS UNIX interface being introduced in the 1990s, the z/OS TSO/ISPF interface remains the dominant means of interaction for z/OS users.
However, as z/OS continues to evolve and embrace modernization, many are transitioning to z/OS UNIX. But, there continues to be a disconnect between users of z/OS UNIX and those accustomed to z/OS TSO/ISPF. In fact, a significant number of inexperienced z/OS UNIX developers often lack familiarity with ISPF and struggle to utilize the full potential of z/OS interactive tools such as IPCS (Interactive Problem Control System).
But what if we could bridge the gap and merge both environments seamlessly to help make ISPF a bit more UNIX friendly?
Streamling z/OS UNIX and z/OS ISPF interactions with c3270 on z/OS
In the past, interacting with z/OS TSO/ISPF and z/OS UNIX required separate sessions and interfaces. One approach was to use a 3270 emulator to connect to TSO/ISPF and then utilize the OMVS command to run z/OS UNIX. However, for most z/OS UNIX developers, the OMVS command proves to be clunky, lacking interactivity, colors, and is downright inefficient. Clearly, a better solution is needed.
Fortunately, with the introduction of zopen community, and specifically z/OS ported tools like c3270, s3270, and x3270if, you can now streamline your interactions with ISPF by communicating from z/OS UNIX to TSO/ISPF within a single z/OS session.
In addition, we will delve into automating ISPF interactions using x3270if and s3270 and discuss the following topics:
- Achieving passwordless interaction with ISPF? Yes (to some extent)!
- Transforming ISPF into a callable API via z/OS UNIX? Absolutely!
What is 3270 and c3270?
c3270 is a terminal emulator specifically designed for accessing and interacting with IBM mainframe systems using the 3270 terminal protocol. The 3270 terminal protocol is a character-based protocol used for communication between IBM mainframes and display devices. It was originally developed in the 1970s and has since become a standard for mainframe terminal emulation.
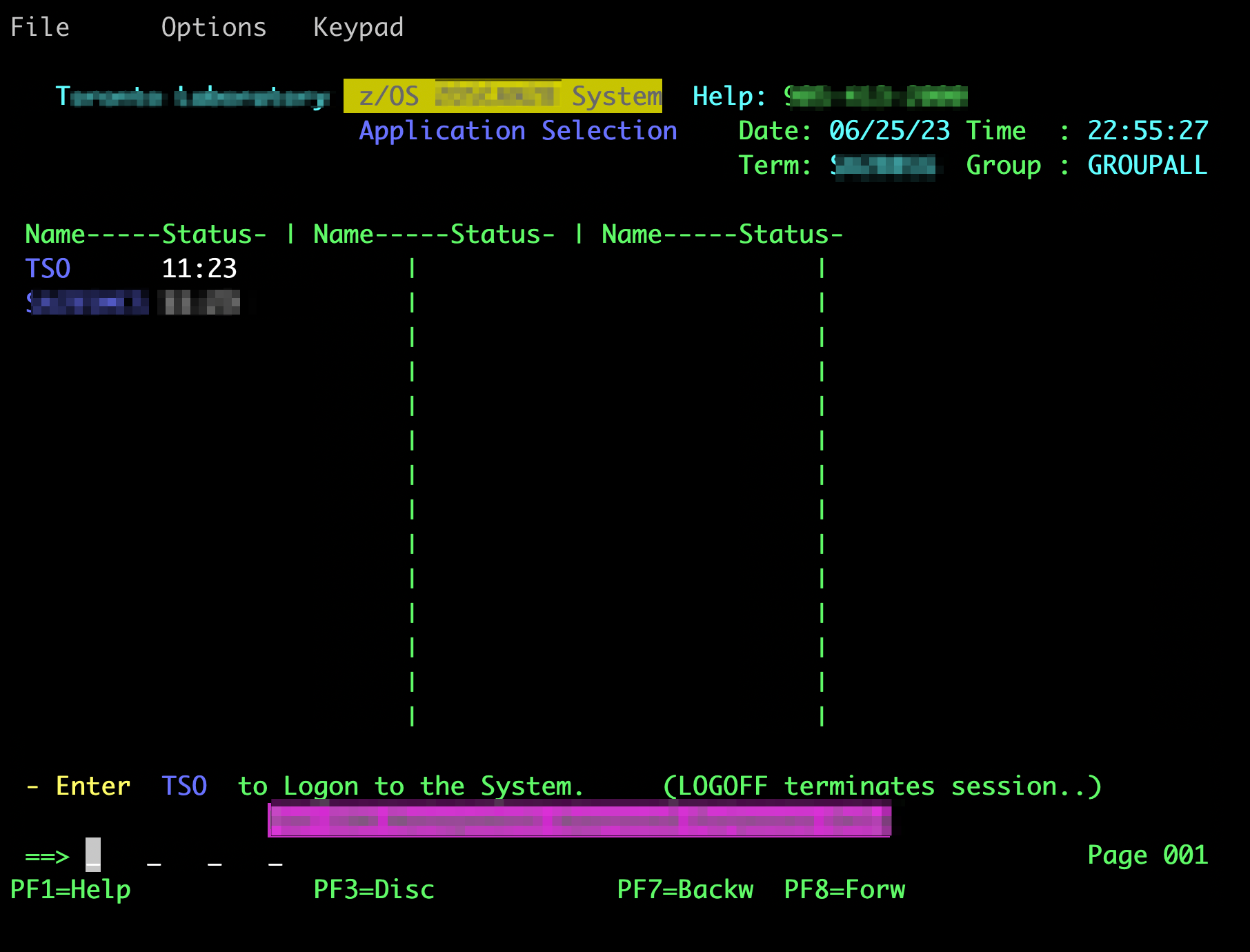
Here’s an example of c3270 running under z/OS UNIX:
Installing c3270
To install c3270 on z/OS UNIX and its utilities, follow these steps:
- Follow the zopen community Getting Started Guide to get the zopen package manager
- Use the
zopencommand to install c3270 by entering:
1
zopen install c3270
Using c3270
Once c3270 is successfully installed, you can begin utilizing its features to interact with z/OS TSO/ISPF. Here’s an example of how to use c3270:
- Launch a terminal session and execute the following command:
1
c3270 <mainframe_hostname>
- Replace
<mainframe_hostname>with the hostname or IP address of your z/OS system.
- Replace
-
Upon establishing the connection, a terminal interface resembling the traditional 3270 mainframe screen will appear. You can now interact with TSO and ISPF commands directly from this session.
-
Enter
TSOto start a TSO/ISPF session. -
Login with your credentials
- Enter
3.4to view a dataset
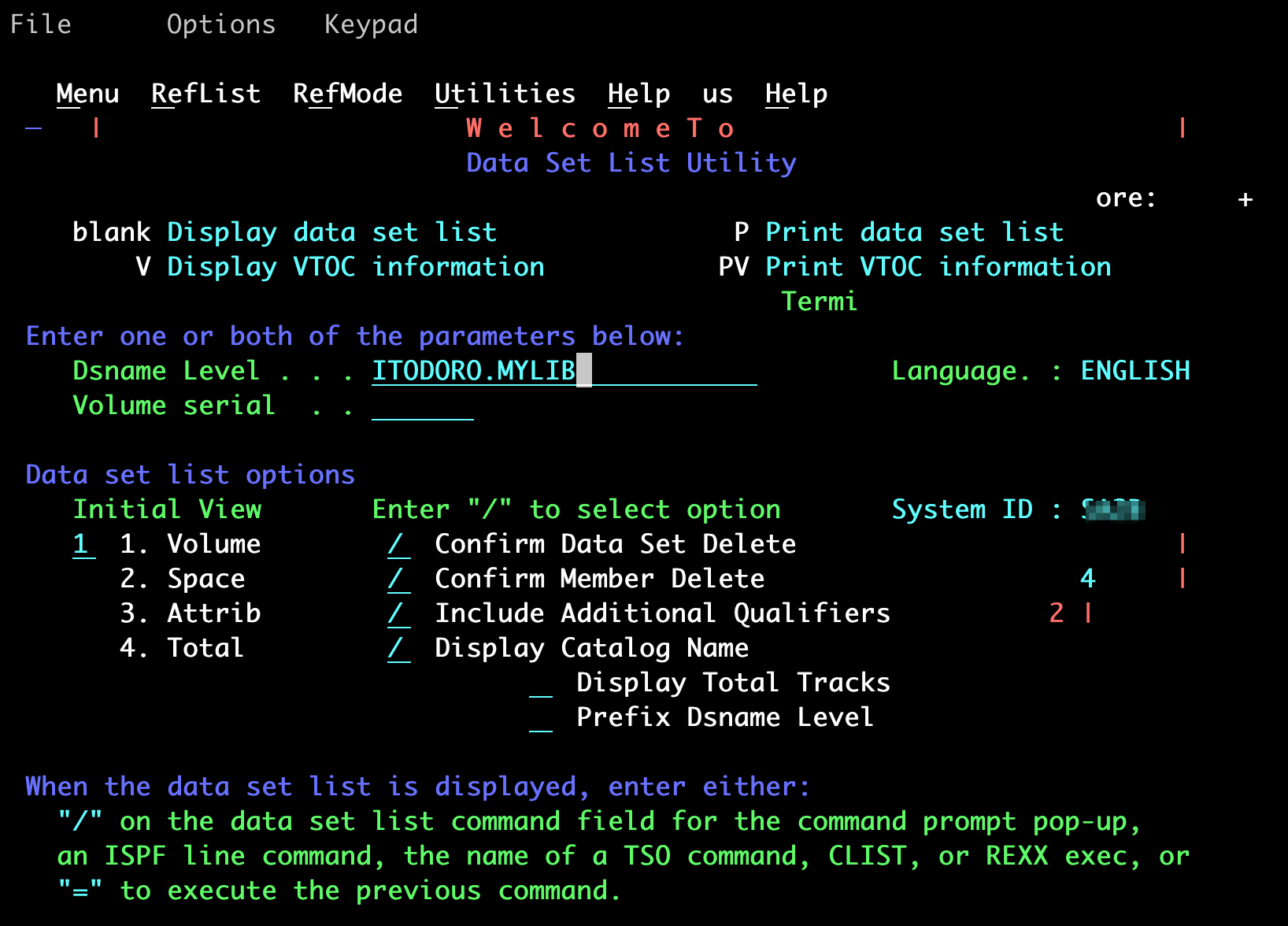
To navigate through ISPF panels, employ the standard 3270 function keys (e.g., PF1, PF3, PF12). For example, press PF3 to return to the previous panel.
While this is great, repeating the login process can become a big productivity bottleneck. Could we potentially automate the login sequence?
Can we automate the login process?
Yes! That’s exactly what the x3270if utility is for. x3270if can send inputs directly to an existing c3270 session. This means that we can automate the login process!
Let’s explore an example of how x3270if can be utilized:
- Begin by creating a shell script, such as
login_ispf.sh, and include the following content:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
if [ -z "$PASSWORD" ]; then
echo "PASSWORD is required for auto login"
exit 1
fi
sendCommands() {
sleep 2
pid=$(ps -ef | grep c3270 | tail -1 | awk '{print $2}')
echo $pid > pid.file
x3270if -p $pid "" >/dev/null
x3270if -p $pid 'wait()'
x3270if -p $pid 'string("tso")'
x3270if -p $pid 'enter()'
x3270if -p $pid 'wait()'
x3270if -p $pid "string(\"$LOGNAME\")"
x3270if -p $pid 'enter()'
x3270if -p $pid "string(\"$PASSWORD\")"
x3270if -p $pid 'enter()'
}
sendCommands &
c3270 -socket localhost
This script sets up a c3270 session and uses x3270if to send inputs from a child process. It starts by connecting to the localhost, waits for a response, then sends the text “tso” and repeats the process for your credentials.
Before running the script, make it executable by running the following command:
1
chmod +x login_ispf.sh
Execute the script by running:
1
2
PASSWORD=$(cat ~/.pass) # set it to your password
./login_ispf.sh
By utilizing x3270if in this manner, you can automate various interactions with z/OS MVS, TSO, and ISPF, saving time and effort.
But why is this useful in the context of z/OS UNIX? Simply put, if there’s a need to interact with both z/OS UNIX and ISPF programs, then this is the perfect utility to automatically trigger those interactions. For example, if you’re building an application in z/OS UNIX and you need to run IPCS to debug to application, you could automatically trigger an IPCS session after a local build via x3270if!
Ok, so we are able to successfully send inputs to ISPF, but can we go the other way? Can we capture the output from an ISPF session and potentially use ISPF as an API? Yes, that is possible as well with s3270!
ISPF as an API? Yes!
Using s3270, we can leverage the power of ISPF by scripting sequences of ISPF interactions and then capturing the contents in text under z/OS UNIX.
For example, if we wanted to capture the contents of the SDSF Operator Console, we can create the following script:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
Connect(localhost)
Wait(InputField)
string("TSO")
enter()
pause()
string("MyId")
enter()
pause()
string("MyPass")
enter()
pause()
enter()
pause()
string("=sdsf")
enter()
pause()
wait()
string("log")
enter()
pause()
ascii()
disconnect
The ascii() command displays the contents in parsable text format.
Change MyId and MyPass to your credentials.
To execute the script, we can pipe it to s3270 as follows:
1
cat inputscript | s3270
You’ll see output like the following:
1
2
3
4
5
6
7
8
9
data: Display Filter View Print Options Search Help
data: -------------------------------------------------------------------------------
data: SDSF SYSLOG 3893.212 MYSYS SA2B 06/26/2023 1W 4,394 COLUMNS 02- 81
data: COMMAND INPUT ===> SCROLL ===> CSR
data: N 4000000 MYSYS 2023177 12:05:00.01 STC08770 00000010 IEF450I MYID1 *OMVSEX
data: N 4000000 MYSYS 2023177 12:05:00.29 STC08770 00000010 IEF450I MYID2 *OMVSEX
data: N 4000000 MYSYS 2023177 12:05:02.23 STC08954 00000010 IEF450I MYID7 *OMVSEX
data: N 4000000 MYSYS 2023177 12:05:08.51 STC08954 00000010 IEF450I MYID9 *OMVSEX
...
As you can see, you can use these steps to automate manual practices involving both z/OS UNIX and ISPF.
Are there any ISPF programs that you would like to call from z/OS UNIX? Let me know in the comments section below!
References:
Special Thanks
I would like to thank CW Cheung for providing inspiration and pointing me to s3270 and x3270if.
-
Previous
Bash on z/OS: My Journey and Contributions -
Next
WeAreDevelopers World Congress - Where Creativity Meets Technology